Aws Rotate Access Keys | Rotate your aws iam user access keys regularly. Aws interface to inactivate keys. Determining when access keys need rotating. Accesskeyid = old_key, username = aws_user, ) raw paste data. You can also change the iam user credentials that atlas uses. Users need their own access keys to make programmatic calls to aws from the amazon web services (aws) sdk for python. You can see the aws secret access key only once immediately after creating. 3 expand the access keys (access key id and secret access key) option. Aws automatic cmk rotation does not require you to update the atlas encryption at rest project enter your iam user's access key id. News, articles and tools covering amazon web services (aws), including s3, ec2, sqs, rds, dynamodb, iam, cloudformation, route 53, cloudfront, lambda, vpc, cloudwatch, glacier and more. How amazon does rotate this temporary credentials? You can also change the iam user credentials that atlas uses. Not only is key rotation a best practice, its definitely something that will be considered during an annual audit. You have 2 access keys associated with your user: Users need their own access keys to make programmatic calls to aws from the amazon web services (aws) sdk for python. Aws interface to inactivate keys. Understanding—and successfully implementing—security concepts is essential to using amazon web services (aws) as your enterprise solution. News, articles and tools covering amazon web services (aws), including s3, ec2, sqs, rds, dynamodb, iam, cloudformation, route 53, cloudfront, lambda, vpc, cloudwatch, glacier and more. You can use access keys to sign programmatic requests to the aws cli or aws api (directly or using the aws to rotate access keys for your own iam user, you must have the permissions from the following policy A typical usage example is automatically updating the access keys for a project's ci/cd service. So, in order to get a secret key, you will need to create a new one. This tool simplifies the rotation of access keys defined in your credentials file. It's good practise to rotate access ids and keys for aws iam users, but a pain to do, this simple script automates the process. It doesn't hurt to rotate your keys every now and then. It's good practise to rotate access ids and keys for aws iam users, but a pain to do, this simple script automates the process. As a security best practice, aws recommends that users periodically regenerate their api access keys. Determining when access keys need rotating. For more information, see signing aws api requests in the amazon web services general reference. Permissions required managing access keys (console) managing access keys (aws cli) managing access keys (aws api) rotating access keys auditing access keys. How are you guys keeping your iam access keys rotated seamlessly? In order to connect to the aws api to make certain required configuration changes, the aws vpc wizard requires access keys to retrieve and modify vpc configurations. Store the new aws key 3. If you don't already have policies describing maximum access key. You can see the aws secret access key only once immediately after creating. You can also change the iam user credentials that atlas uses. It includes the following steps: You can use access keys to sign programmatic requests to the aws cli or aws api (directly or using the aws to rotate access keys for your own iam user, you must have the permissions from the following policy It might seem scary, but if you keep your keys only locally it's a two minute job to swap them over. Ensure aws iam access keys are rotated on a periodic basis as a security best practice (90 days). In this course, instructor sharif nijim couples pragmatic advice with practical examples that show it pros how to create a secure infrastructure within aws. News, articles and tools covering amazon web services (aws), including s3, ec2, sqs, rds, dynamodb, iam, cloudformation, route 53, cloudfront, lambda, vpc, cloudwatch, glacier and more. In order to connect to the aws api to make certain required configuration changes, the aws vpc wizard requires access keys to retrieve and modify vpc configurations. This allows easier automation of key rotation for required services. User is not being recreated in aws upon removing credentialsrequest. Understanding—and successfully implementing—security concepts is essential to using amazon web services (aws) as your enterprise solution. You can use access keys to sign programmatic requests to the aws cli or aws api (directly or using the aws to rotate access keys for your own iam user, you must have the permissions from the following policy Use azure key vault to manage and rotate your keys securely. It includes the following steps: In this course, instructor sharif nijim couples pragmatic advice with practical examples that show it pros how to create a secure infrastructure within aws. In order to connect to the aws api to make certain required configuration changes, the aws vpc wizard requires access keys to retrieve and modify vpc configurations. Users need their own access keys to make programmatic calls to aws from the amazon web services (aws) sdk for python. Ensure aws iam access keys are rotated on a periodic basis as a security best practice (90 days). Other cloud compliance vendors will tell you to rotate keys every 90 days. Aws access key security is hard. Store the new aws key 3. How are you guys keeping your iam access keys rotated seamlessly? What is aws access key rotation? Rotate your aws iam user access keys regularly. And then the aws security team wrote up a long blog post about how to rotate your keys.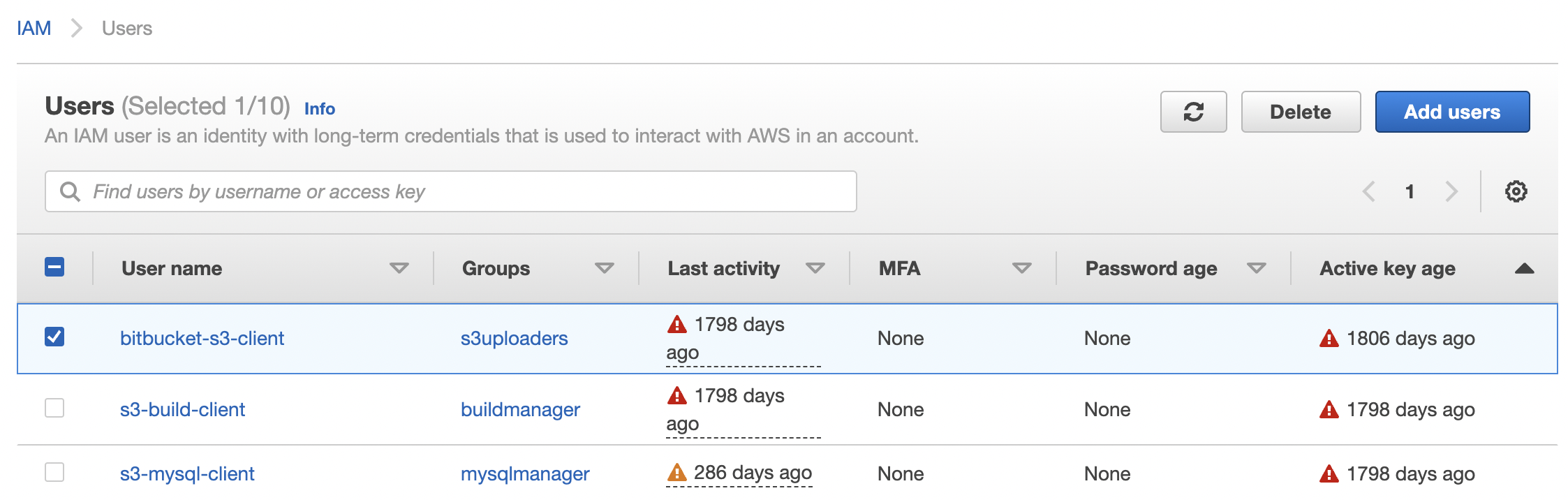


Aws Rotate Access Keys: Ensure aws iam access keys are rotated on a periodic basis as a security best practice (90 days).
Source: Aws Rotate Access Keys

EmoticonEmoticon